Fascination About Aws Backup
Wiki Article
Rto for Beginners
Table of ContentsIndicators on S3 Cloud Backup You Need To KnowHow Aws Cloud Backup can Save You Time, Stress, and Money.Unknown Facts About Data ProtectionThe Basic Principles Of Ransomware Protection Ec2 Backup - Truths
Keeping several suppliers as well as systems along with typical computer has placed wonderful stress on IT divisions. Going ahead, data defense should have the ability to adapt to these currently complicated scenarios. Information security approaches are created to secure data, maintain privacy and stop data loss as well as corruption without trading them for evaluation as well as testimonial.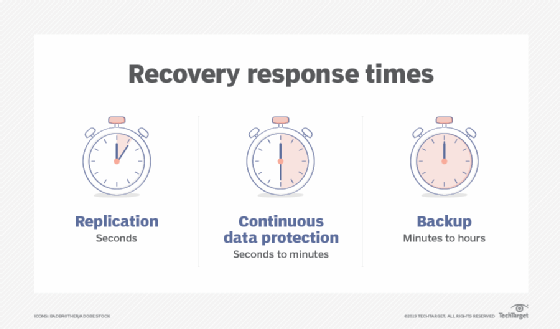
Information erasure techniques likewise validate the data can not be recuperated. Gain access to administration regulates guarantee information honesty by restricting accessibility to electronic assets.
Besides, a lot of the world's communications and service takes place in the cloud or via personal devices in remote work atmospheres. The most effective information defense remedies combine durable protection procedures with human procedures as well as process. The overall goal: to guarantee data protection is taken into consideration early during the electronic details life process.
S3 Cloud Backup Fundamentals Explained
Information safety is everybody's business, so, it's likewise essential to ensure regular, recurring protection recognition training is component of your data defense technique. Information personal privacy defines that has accessibility to data, while information security supplies tools and also policies to in fact restrict accessibility to the information.It plays an essential role in service operations, advancement, and also finances. Data defense services rely on technologies such as information loss avoidance (DLP), storage with built-in information protection, firewall softwares, security, and endpoint security.
It is occasionally also called information protection. A data security method is vital for any type of company that accumulates, handles, or stores sensitive data. An effective strategy can assist protect against information loss, theft, or corruption as well as can assist decrease damages created in case of a violation or disaster. Data security concepts assist shield information and make it available under any type of scenarios.
More About Aws Backup
Here are crucial data management facets pertinent to data protection: ensuring users can access and utilize the information called for to do company also when this information is shed or harmed. involves automating the transmission of vital data to offline and also online storage. entails the evaluation, cataloging, as well as security of details possessions from numerous sources, consisting of facility outages as well as disturbances, application and also individual mistakes, maker failure, and malware and also infection strikes.Data privacy is usually used to personal health details (PHI) and directly identifiable info (PII). This includes economic information, medical records, social protection or ID numbers, names, birthdates, and call information. Data privacy worries put on all sensitive information that organizations manage, consisting of that of customers, shareholders, as well as staff members. Frequently, this info plays a crucial function in service procedures, growth, and also financial resources.
It protects against bad guys from being able to maliciously make use of data and helps ensure that companies satisfy regulative demands. Data protection regulations govern how particular information types are accumulated, transferred, as well as used. Individual information includes various kinds of details, consisting of names, pictures, email addresses, checking account information, IP addresses of computers, and biometric information.

The Of Ec2 Backup
Furthermore, each legislation has various conditions that may apply to one situation yet not an additional, and also all regulations go through modifications. This level of complexity makes it challenging to execute compliance continually and properly. Both information defense and also privacy are important as well as the 2 commonly come with each other, these terms do not stand for the exact same thing.Data personal privacy specifies the policies that information protection devices and also procedures use. You can restrict accessibility with data protections while still leaving delicate data vulnerable.
For protection, it depends on the business managing data to make certain that it stays private. Compliance laws show this difference as well as are created to assist make sure that individuals' privacy demands are passed by companies. When it pertains to safeguarding your information, there are lots of storage space as well as management options you can select from (aws cloud backup).
Here are several of the most frequently made use of methods and modern technologies: an initial step in information defense, this entails discovering which data sets exist in the organization, which of them are service critical see here now and which consists of delicate information that could be based on compliance laws (aws backup). a set of techniques as well as tools that you can use to stop data from being stolen, lost, or unintentionally erased.
The smart Trick of Ec2 Backup That Nobody is Discussing
modern-day storage tools supplies built-in disk clustering and also redundancy. For instance, Cloudian's Hyperstore gives up to 14 nines of resilience, affordable making it possible for storage of huge quantities of data, and also quick accessibility for very little RTO/RPO. Learn a lot more in our overview to. develops copies of information and also stores them independently, making it feasible to restore the information later on in instance of loss or modification.Report this wiki page